Introduction
Azure Role-Based Access Control (Azure RBAC):
Effective access management for cloud resources is a vital responsibility for any organization utilizing cloud services.
Azure Role-Based Access Control (Azure RBAC) serves as an authorization framework integrated with Azure Resource Manager, delivering precise control over who can access Azure resources, what actions they can perform on these resources, and the specific areas within Azure they can access.
Azure RBAC offers fine-grained access management, ensuring that access privileges are aligned with roles and responsibilities, thereby enhancing security and operational efficiency.
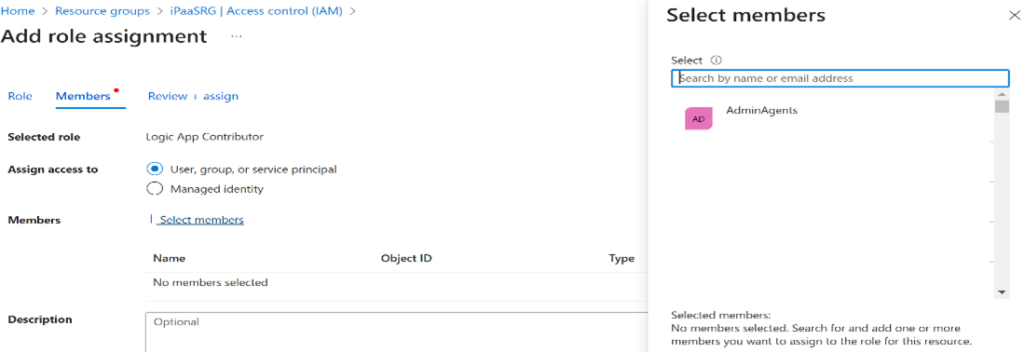
Role-Based Access Control (RBAC) in Azure Logic Apps allows you to control access to Logic App resources and actions within your Logic App workflows. RBAC enables you to assign roles to users, groups, or service principals, which determines what they can do with Logic Apps.
Here’s how you can implement RBAC for Logic Apps:
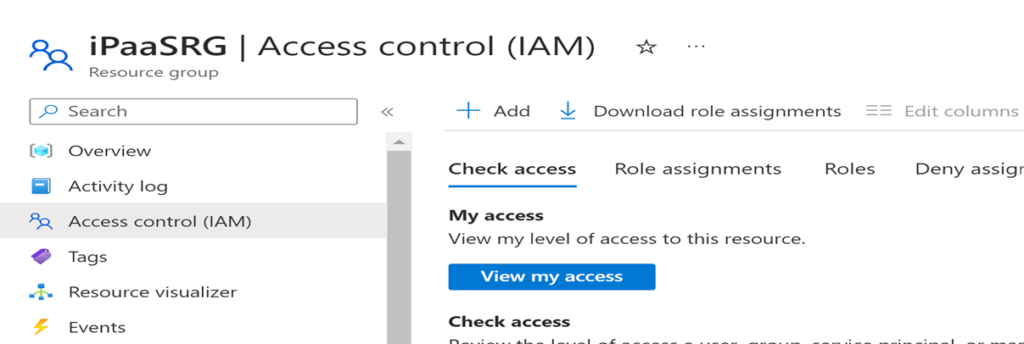
Verification:
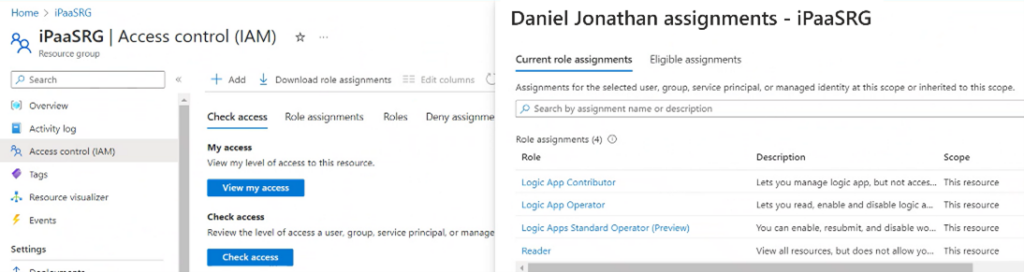
Verify Role Assignment
To verify that the role assignment is working as expected, you can sign in as the user or service principal that you granted access to and attempt to perform actions in the Logic App. The user should only be able to perform actions that are allowed by the assigned role.
Keep in mind, you can also create custom roles if the built-in roles don’t meet your specific requirements.
Automate Logic Apps RBAC
If you prefer to automate Logic Apps RBAC with Azure Bicep, you can use the provided Bicep code snippet. It allows you to assign RBAC roles programmatically by specifying the principal, role, and other parameters.
param principalId string
@allowed([
'Device'
'ForeignGroup'
'Group'
'ServicePrincipal'
'User'
''])
param principalType string = ''
@allowed([
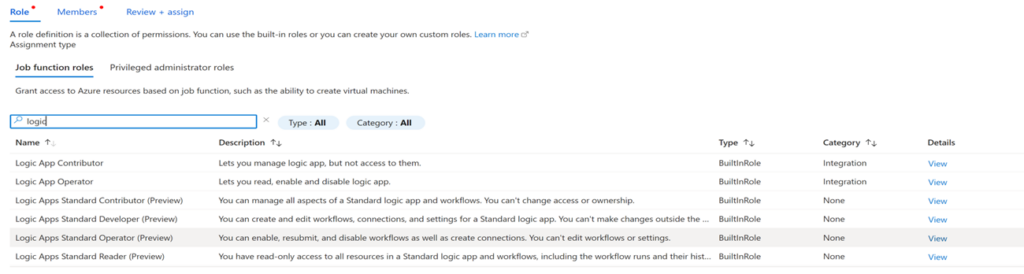
'Logic App Contributor'
'Logic App Operator'
'Logic Apps Standard Contributor (Preview)'
'Logic Apps Standard Developer (Preview)'
'Logic Apps Standard Operator (Preview)'
'Logic Apps Standard Reader (Preview)'
])
param roleDefinition string
var roles = {
// See https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles for these mappings and more.
'Logic App Contributor': '/providers/Microsoft.Authorization/roleDefinitions/87a39d53-fc1b-424a-814c-f7e04687dc9e'
'Logic App Operator': '/providers/Microsoft.Authorization/roleDefinitions/515c2055-d9d4-4321-b1b9-bd0c9a0f79fe'
'Logic Apps Standard Contributor (Preview)': '/providers/Microsoft.Authorization/roleDefinitions/ad710c24-b039-4e85-a019-deb4a06e8570'
'Logic Apps Standard Developer (Preview)': '/providers/Microsoft.Authorization/roleDefinitions/523776ba-4eb2-4600-a3c8-f2dc93da4bdb'
'Logic Apps Standard Operator (Preview)': '/providers/Microsoft.Authorization/roleDefinitions/b70c96e9-66fe-4c09-b6e7-c98e69c98555'
'Logic Apps Standard Reader (Preview)': '/providers/Microsoft.Authorization/roleDefinitions/4accf36b-2c05-432f-91c8-5c532dff4c73'
}
var roleDefinitionId = roles[roleDefinition]
resource roleAuthorization 'Microsoft.Authorization/roleAssignments@2022-04-01' = {
// Generate a unique but deterministic resource name
name: guid('la-rbac', resourceGroup().id, principalId, roleDefinitionId)
scope: resourceGroup()
properties: {
principalId: principalId
roleDefinitionId: roleDefinitionId
principalType: empty(principalType) ? null : principalType
}
}
Conclusion
Take Action!
By implementing Azure RBAC for Logic Apps, the organization can achieve efficient, secure, and compliant management of their workflow automation processes while accommodating the needs of various teams and individuals within their organization.
Interested in our
Approach & Solutions?
Don’t settle when it comes to making critical decisions.
Get in Touch – and explore the possibilities!
Seamless Integrations
Customer centricity
Microsoft Partner
Tailor-made solutions
Industry Pioneer
Agile Approach
Data Insights
Architecture Excellence
Experience