Problem Statement: In a microservices architecture, individual services require secure authentication mechanisms. However, implementing built-in authentication for each container app in a decentralized manner becomes impractical and lacks a centralized approach.
Solution: Utilize containerized Azure API Management (APIM) to establish a centralized authentication mechanism for securing and exposing microservices APIs to the external world. This approach ensures a more flexible and scalable deployment.
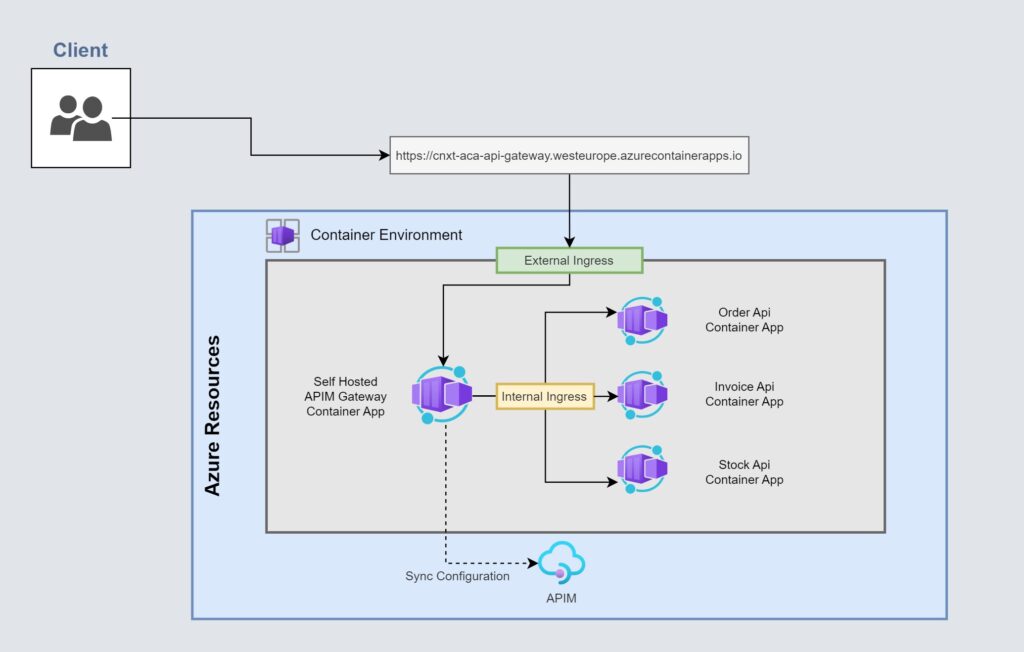
Architecture Components:
Azure Container Apps:
- Azure Container Apps provides a serverless container service that allows you to run containers without managing the underlying infrastructure.
Microservice:
- Each microservice is packaged as a Azure Container App, encapsulating the application code, dependencies, and runtime environment.
Azure APIM Instance:
- Enable the self-hosted gateway; onboarding APIs and implementing policies to effectively manage and govern their behavior.
Containerized APIM Gateway:
Deploy Azure API Management Gateway as a container to centralize authentication and security.
Benefits:
Centralized Security:
- Ensures a unified and centralized authentication approach for all microservices APIs
Scalability:
- Scales seamlessly to meet varying workloads and demands of microservices architecture.
Simplified Management:
- Streamlines the management of authentication and security policies across multiple microservices.
Leverage APIM Gateway:
- APIM gateways are instrumental in fortifying API ecosystems, ensuring security, optimizing traffic, and offering crucial tools for monitoring and performance enhancement, this contributes to the resilience and reliability of the overall API infrastructure
Conclusion
Take Action!
Implementing containerized Azure API Management addresses the challenge of securing and exposing microservices APIs in a decentralized environment. This approach offers centralized authentication, flexibility, scalability, and simplified management, ensuring robust security for the microservices architecture.
Interested in our
Approach & Solutions?
Don’t settle when it comes to making critical decisions.
Get in Touch – and explore the possibilities!

Leave a Reply